A OWASP vulnerabilities and open surface scan of more than two thousands websites in National cyber perimeters of different countries has been carried out to generate data for 5 KPIs to rank the different cyber perimeters in a global cybersecurity index. Cyber perimeter is defined by websites of institutional, private companies and services and supply chain operating in a country or for its citizen. The countries in this analysis: Turkey🇹🇷, Italy🇮🇹, India🇮🇳, Brazil🇧🇷, Argentina🇦🇷 and Indonesia🇮🇩. A comparison of national cyber security perimeters of different countries based on Key Performance Indicators, which weighted are used to calculate the security score of a country.
The 5 Key Performance Indicators analysed in this study are presented as the following questions:
- Which percentage of websites in cyber perimeters can be reached from the TOR network?
- What is the number of services running on open ports found in websites in cyber perimeters?
- What are the top exposed services found in cyber perimeters of analysed countries?
- What are number of high/medium/low/informational vulnerabilities found with a passive scan for websites in cyber perimeters?
- What are the most detected OWASP vulnerabilities with a passive scan for websites in cyber perimeters?
Which percentage of websites in cyber perimeters can be reached from the TOR network?
TOR or The Onion Router is a type of internet network that allows for anonymous communication. Through TOR the origin of traffic is obfuscated and it is more difficult to trace users through it given the high number of nodes which the connection passes through and anonymising techniques – like removing referral headers – which make it very difficult to properly identify the routes of online behaviour as the traffic is relayed through a network of more than 7000 global nodes. Also many DDOS attacks and other illegal activities (TOR can also be used for legit purposes) are relayed via the TOR network to make tracing more difficult to understand and pursue its origin with regards to malicious actors. Therefore allowing traffic from a TOR node to a site in the cyber perimeter, and the site allowing the connection and replying with the same page as it would to a non-TOR connection increases the attack surface of the cyber perimeter of a country.
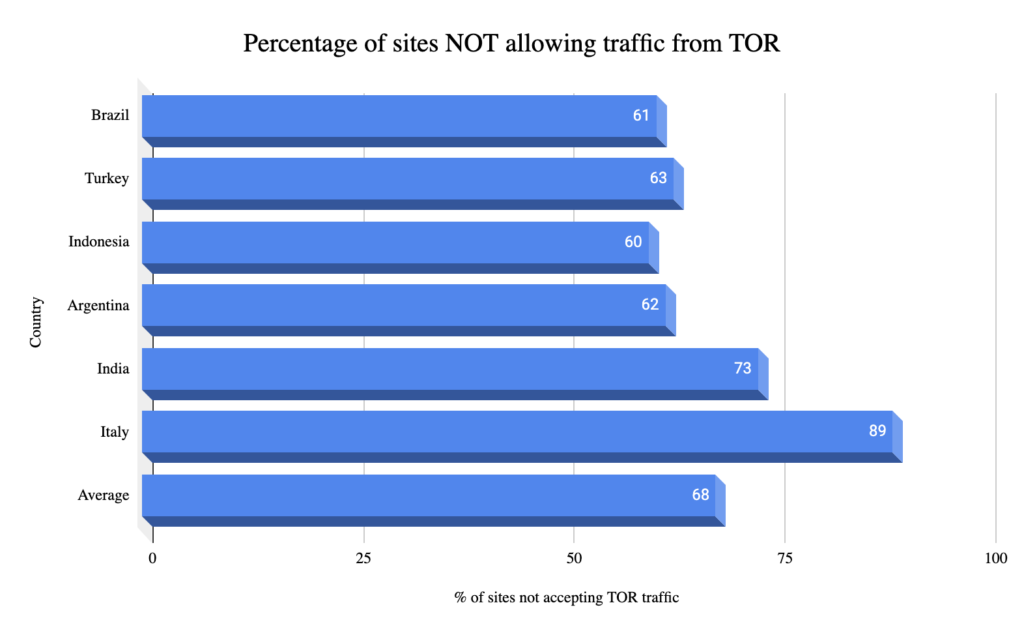
The analysis carried out through the AWS cloud of the thousands of sites from the different perimeters grouped by country with the related percentages of sites tested not allowing traffic from the TOR network, hence decreasing the attack surface and increasing security.
What is the number of services running on open ports found in websites in cyber perimeters?
In order to serve a website at least 1 port must be opened on the server hosting the site, this usually is port 80 for HTTP and port 443 for HTTPS. The more services that are exposed on a host with open ports, the greater the attack surface it is for that website. Therefore the national cyber perimeter that has the most open ports on its websites is at a higher risk of damage if attacked. Only necessary ports should be opened and an IP quality scoring should be used. In this shallow scan ports are not filtered if they are “fake” open by a firewall.
The number of services with open ports per country without normalisation, hence impacted by the number of sites in the cyber perimeter scanned:
| Country | Unique raw number of services with open ports |
| Brazil | 12 |
| Turkey | 39 |
| Indonesia | 29 |
| Argentina | 22 |
| India | 12 |
| Italy | 75 |
| Average | 30 |
Some services need to keep ports open to work and function, yet the best practice for security would be to keep as many services as possible secured behind a Virtual Private Network or institution VPNs where access are filtered through an access control list with a deny by default and least privileges allocated to user and increased on a per need basis.
What are the top exposed services found in cyber perimeters of analysed countries?
Exposed services are web services that are running on open ports, the more exposed services the greater the attack surface that a web site has. Even though some service must be exposed to serve the website from its domain name (the url address), its always appropriate to limit these services and the review the exposed ones frequently to make sure none are inadvertently set to be accessed from the whole internet, also a good idea is to use different non indexable domain names for different services, like email or FTP. Even better is to expose those service only behind a VPN. The following table shows the top exposed services, excluding HTTP and HTTPS endpoints and ports pretending to be open by a firewall on sites in the cyber perimeter of a country. The following table presents these results.
| Country | Top 3 exposed services in cyber perimeter excluding HTTP, HTTPS and fake open ports |
| Brazil | 1. Cisco SCCP 2. Session Initiation Protocol 3. DNS |
| Turkey | 1. SMTP 2. Cisco SCCP 3. POP3 |
| Indonesia | 1. SMTP 2. SSH 3. DNS |
| Argentina | 1. SMTP 2. POP3 3. FTP |
| India | 1. SMTP 2. POP3 3. IMAP |
| Italy | 1. SMTP 2. FTP 3. POP3 |
The most used protocols identified and services found (excluding HTTP and HTTPS) are detailed below:
SMTP: The Simple Mail Transfer Protocol is a Web standard communication convention for email transmission. Mail servers and other message exchange specialists utilize SMTP to send and get mail messages. Port 25 is the first standard mail SMTP harbour and the most seasoned, since it to begin with debuted in 1982. Nowadays, the IANA on of the organizations capable for keeping up the web, still recognizes Port 25 as the standard default SMTP port.
The Session Initiation Protocol or SIP is a messaging/signaling protocol used for starting, keeping up, and ending communication sessions that incorporate voice, video and data services. SIP is utilized in Web communication, in private IP phone frameworks, as well as portable phone calling over LTE networks. SIP works in conjunction with a few other conventions that indicate and carry the session media. Most commonly, media sort and parameter transaction and media setup are performed with the Session Description Protocol (SDP), which is carried as payload in SIP messages. For secure transmissions of SIP messages over insecure networks, the SIP messages may be scrambled with Transport Layer Security (TLS). For the transmission of media streams (voice, video) the SDP payload carried in SIP messages regularly utilizes the Real-time Transport Protocol (RTP).
The Skinny Client Control Protocol (SCCP) is a proprietary control protocol, a lightweight IP-based convention for session signaling via the Cisco Unified Communications Manager. The protocol architecture is comparable to the media portal control convention design, in that’s breaks down the work of media transformation in media transmission for transmission through a Web Protocol arranged into a generally low-end customer-premises devices and a call specialist usage that controls the communication by means of signaling commands.
The Domain Name System (DNS) is a progressive and dispersed naming system for computers, administrations, and other assets within the Web or other Web Protocol (IP) systems. It partners different data with domain names/urls associated to each of the related service. Most unmistakably, it interprets promptly memorized space names to the numerical IP addresses required for finding and recognizing computer servers and internet connected devices. The DNS has been a fundamental component of the Web since 1985.
Post Office Protocol (POP3) is an application-layer Web standard convention utilized by email clients to recover email from a mail server. POP form 3 is in common use, and one of the foremost common conventions for e-mail recovery. The STARTTLS expansion permits the use of Transport Layer Security (TLS) or Secure Attachments Layer (SSL) to be arranged utilizing the STLS on the POP3 service. The protocol underpins download and erase operations for messages. POP3 clients interface, recover all messages, store them on the client computer, and can erase them from the server.
The File Transfer Protocol (FTP) may be a standard communication convention utilized for the exchange of computer records from a server to a client on a computer organize. FTP is built on a client–server design utilizing partitioned control and information associations between the client and the server. FTP clients may confirm themselves with a clear-text sign-in convention, regularly within the frame of a username and secret word, but can interface namelessly on the off chance that the server is arranged to permit it. For secure transmission that secures the username and secret word, and scrambles the substance, FTP is regularly secured with SSL/TLS (FTPS) or supplanted with SSH File Transfer Protocol (SFTP).
The Secure Shell Protocol (SSH) is a cryptographic technology for working network services safely over an unsecured network. Its most striking applications are inaccessible login and command-line execution. SSH applications are based on a client–server engineering, interfacing an SSH client occurrence with an SSH server. SSH works as a layered convention suite comprising three central progressive components: the transport layer gives server confirmation, secrecy, and judgment; the client verification convention approves the client to the server; and the connection convention multiplexes the scrambled burrow into different consistent communication channels.
The Internet Message Access Protocol (IMAP) is a Web standard convention utilized by mail clients to recover mail messages from a mail server over a TCP/IP connection. IMAP was planned with the objective of allowing total administration of an e-mail box by different e-mail clients, hence clients for the most part take off messages on the server until the client unequivocally erases them. An IMAP server regularly tunes in on port number 143. IMAP over SSL/TLS (IMAPS) is relegated the port number 993.
Parts of descriptions from online sources.
What are the percentages of high/medium/low/informational vulnerabilities found with a passive scan for websites in cyber perimeters?
OWASP or Open Web Application Security Project is a collection of tools and guidelines to define web application and computer security, OWASP produces a list of top 10 security vulnerabilities found in web apps. In order to understand which vulnerabilities are most present in the cyber perimeter of a country a scan must be made, scans can be passive or active with passive scans being non invasive. A passive scanning method with ZAP has been used to highlight these vulnerabilities in sites of the perimeter, this limits the number of vulnerabilities identified to exclude high ones and only include informational, low and middle vulnerabilities from the OWASP list.
The number of identified vulnerabilities of types informational, low and medium are normalised over the total number of sites analysed per country. Following results were identified:
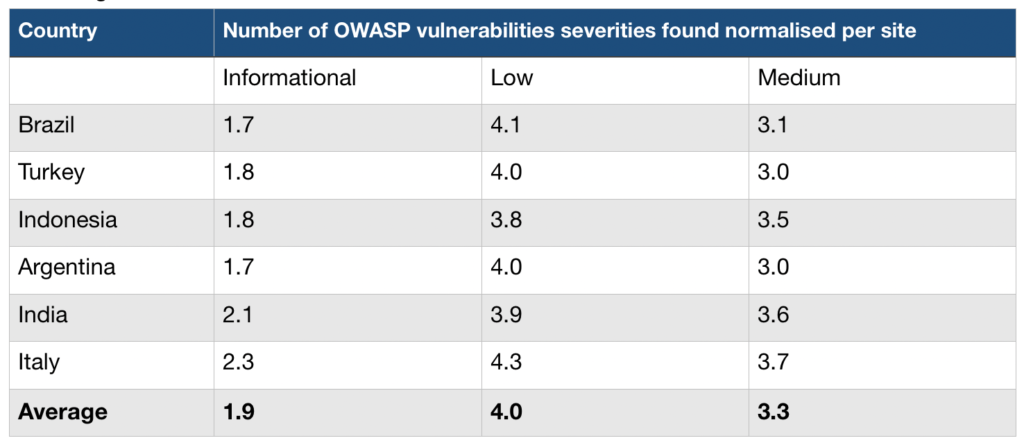
OWASP alerts categories definitions are as follows:
- Informational: presents most often as an information disclosure, like showing a server version or sensitive information included in a url hardcoded or credentials, possible username enumeration. Also informational are security recommendations, for example to re examine cache directives to make sure nothing confidential is cached.
- Low: these alerts include private IP disclosure, non secure cookies, content security policies (CSP) minor config errors, some content headers missing, to name a few. Low alerts can be used to gather more information on a site for OSINT purposes or further penetration testing.
- Medium: these alerts can include buffer and integer overflow vulnerabilities found in the site, carriage return and/or line feed (CRLF) Injection. CRLF injection can be dangerous whereas a message sent to the server including a line break or new line and then more data or a command could be executed if the text is not properly filtered server side. Medium alerts can include also parameter tampering and Server Side Includes and backup file disclosure
- High: these alerts are the most dangerous ones and tested usually with an active scan, which was not performed in this analysis. High alerts include the Heartbleed OpenSSL vulnerability, path traversal – which is dangerous because it means the files on the server are exposed, remote file inclusion and SQL injection, which can reveal and or alter the contents of the database associated with the site.
What are the most detected OWASP vulnerabilities with a passive scan for websites in cyber perimeters?
Top 3 OWASP informational/low/medium vulnerabilities identified via passive (no malicious payload is sent to the site) scan per country, by number of occurrences. An explanation of each is presented as per the OWASP official definition in the table below.
| Severity | Vulnerability/Risk | Description |
| Medium | Content Security Policy (CSP) Header Not Set | Headers that define approved sources of content that browsers should be allowed to load on that page — covered types are JavaScript, CSS, HTML frames, fonts, images |
| Low | X-Content-Type-Options Header Missing | Can cause the response body to be interpreted and displayed as a content type other than the declared content type |
| Informational | Re-examine Cache-control Directives | The resources loaded should be reviewed to ensure that no sensitive content will be cached |
| Informational | Information Disclosure – Suspicious Comments | The response appears to contain suspicious comments which may help an attacker |
| Medium | Absence of Anti-CSRF Tokens | A cross-site request forgery or CSRF is an attack that involves forcing a victim to send an HTTP request to a target destination without their knowledge or intent in order to perform an action as the victim. Without these tokens the trust of the website for the user is abused |
A list of countries currently analysed with related top 3 informational/low/medium OWASP vulnerabilities identified can be found in the table below.
| Country | Top 3 OWASP vulnerabilities found in cyber perimeter sorted by occurrence |
| Brazil | 1. Content Security Policy (CSP) Header Not Set 2. X-Content-Type-Options Header Missing 3. Re-examine Cache-control Directives |
| Turkey | 1. Content Security Policy (CSP) Header Not Set 2. X-Content-Type-Options Header Missing 3. Re-examine Cache-control Directives |
| Indonesia | 1. Content Security Policy (CSP) Header Not Set 2. Information Disclosure – Suspicious Comments 3. X-Content-Type-Options Header Missing |
| Argentina | 1. Content Security Policy (CSP) Header Not Set 2. X-Content-Type-Options Header Missing 3. Re-examine Cache-control Directives |
| India | 1. Information Disclosure – Suspicious Comments 2. Content Security Policy (CSP) Header Not Set 3. Re-examine Cache-control Directives |
| Italy | 1. Content Security Policy (CSP) Header Not Set 2. Information Disclosure – Suspicious Comments 3. Absence of Anti-CSRF Tokens |
These vulnerabilities or risks increase the attack surfaces of the cyber perimeters of the country taken into consideration.
